
Hackers could hijack user accounts in dozens of fitness and gym mobile applications, even where the two-factor authentication (2FA) mechanism was active.
The common ground for all the apps is Fizikal, a management platform from Israel for gyms and sports clubs that allows customers to handle their subscription and class registration.
Several vulnerabilities affecting the Fizikal platform could be chained to bypass security checks, enumerate users, bruteforce the one-time password (OTP) for logging in, and get access to a user's account.
Easy brute force
Sahar Avitan, a consultant at Israel-based boutique cybersecurity firm Security Joes, discovered that about 80 apps relied on Fizikal's API to ensure easier access to the club and amenities available.
At the time of writing, there are close to 70 Fizikal apps in Google Play Store's health and fitness section, many of them added over the past few days. Some of the older apps have upwards of 5,000 downloads and together account for at least 240,000 active installations.
Avitan's interest in analyzing the platform was piqued after he reset the password for his EZ Shape account one of the apps he used and noticed that he received a weak, 4-characters one.
One thing the researcher noticed was that the password reset procedure returned different results for phone numbers present in the database than non-existent ones.
This allowed him to better understand the entire mechanism, leading to bypassing security checks and being able to enumerate users. This information allowed him to learn the phone numbers that users defined to receive the OTP password over SMS to confirm the reset.
However, another flaw made it possible to brute force the OTP numbers (process completes in about one minute) and send them to Fizikal API before the legitimate user received the alert.
According to Security Joes, the OTP verification process was undefended by an anti-automation mechanism or captcha that would block the brute-force attempts.
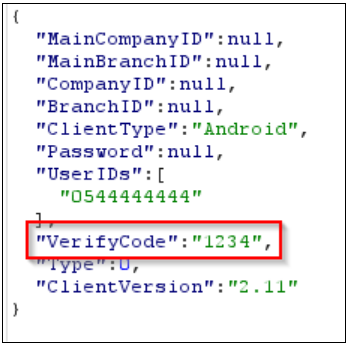
With the OTP in hand, Avitan sent it to the Fizikal server and received a unique TokenID necessary for generating a new password. He delivered the code to the server in HTTP headers along with a fresh password.
Hijacking an app account for an app that relies on Fizikal management platform not only allowed an attacker to lock the user out or cancel their subscription but also granted access to personally identifiable information:
- phone number
- full name
- date of birth
- email address
- postal address
- ID number
Avitan was able to automate the entire procedure with proof-of-concept code that exploited the flaws he discovered in Fizikal
Ido Naor, founder and CEO of Security Joes, told BleepingComputer that an ill-intended individual could have leveraged these vulnerabilities to learn the schedule of someone famous or a member of the government.
According to the researchers, Fizikal and the CERT in Israel received a full report about the findings and acted quickly to address the issues.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now